Shin Bet Thwarts 85 Iranian Cyber Attacks on Israeli Public Figures
Targeted phishing campaigns aimed at security officials, politicians, academics and journalists were designed to gather personal intel for potential attacks

Israel’s Shin Bet security agency and the National Cyber Directorate have thwarted 85 attempted Iranian cyberattacks in recent months, aimed at high-profile Israeli civilians and public servants, including security officials, politicians, academics, journalists, and media personalities.
According to a statement released Wednesday, Iranian operatives have dramatically increased their use of phishing tactics—posing as journalists, researchers, or professionals on WhatsApp, Telegram, and email, in order to extract sensitive login credentials from targets.
These credentials, once obtained, are used to access personal Gmail accounts, cloud-stored images, location data, and even passwords for other services, allowing hostile actors to map the routines, relationships, and vulnerabilities of key Israeli figures.
Shin Bet officials emphasized that the ultimate purpose of the cyber campaigns is to gather intelligence for physical attacks inside Israel, possibly using domestic operatives recruited and activated by Iran.
One common method involves fake invitations to Google Meet calls, where the victim is prompted to enter login credentials on a spoofed page, granting the attacker full access to their Google ecosystem.
Other attack vectors include:
A Shin Bet official warned:
“This is part of Iran’s ongoing war against Israeli society, and these attacks can be prevented with proper cyber hygiene—avoiding unknown links, staying alert, and never sharing credentials with unverified sources.”
Authorities urged the public, especially those in public roles, to remain vigilant and suspicious of unsolicited messages, and to report any suspicious communications to Israel’s cyber response centers.
The Shin Bet reaffirmed its commitment to preemptively detecting and neutralizing Iranian cyber operations before harm can be done.
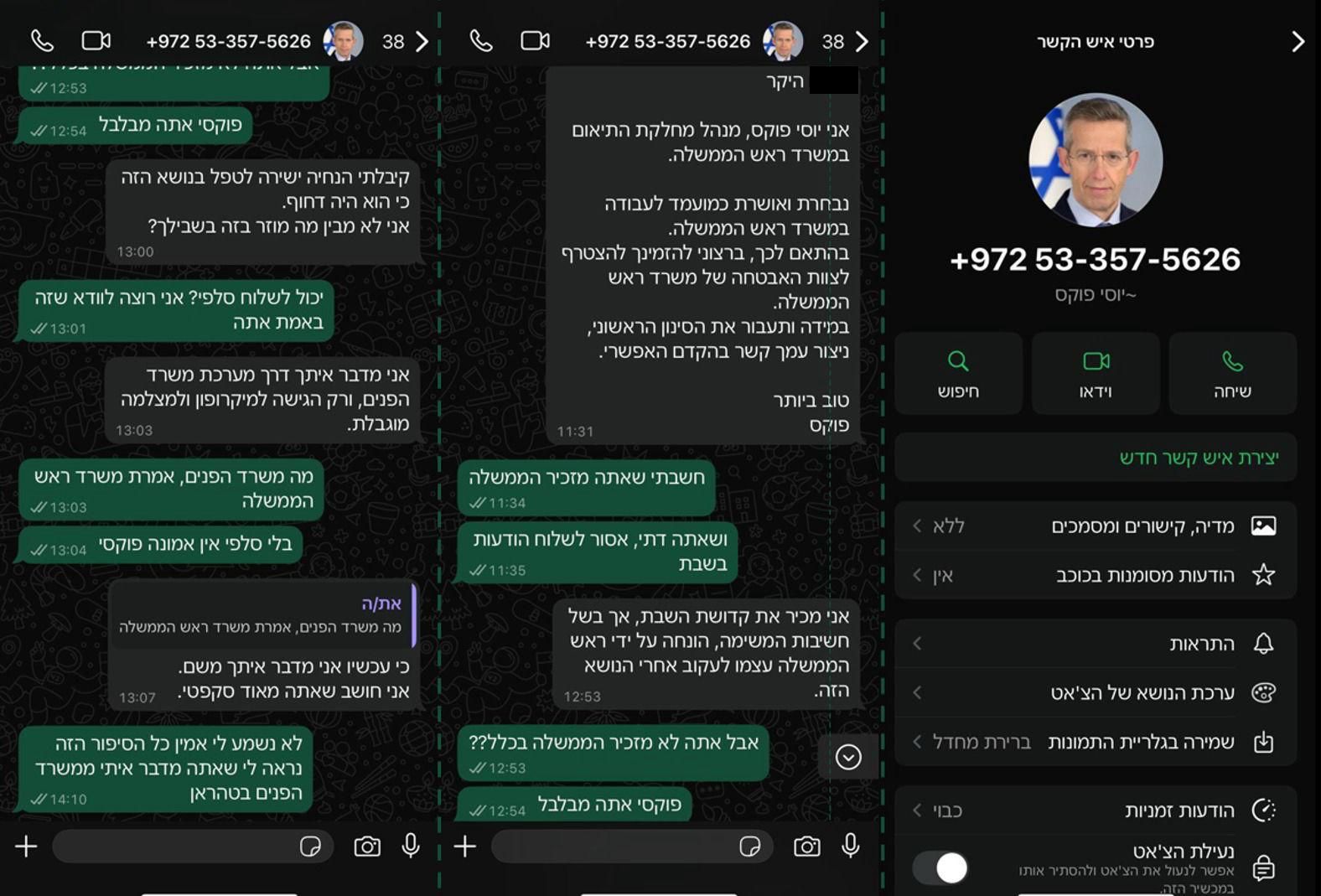
Example: Iranian Impersonator Poses as Cabinet Secretary in Failed Phishing Attempt
In one documented case shared by security officials, an Iranian operative impersonated Israeli Cabinet Secretary Yossi Fuchs in an attempt to deceive an Israeli citizen. The fake communication—conducted via messaging apps—sought to extract sensitive information under the guise of an official request.
Thanks to the citizen’s cautious behavior and timely report to authorities, the phishing attempt was promptly identified and neutralized before any damage occurred.
Officials noted that this case underscores the importance of public awareness and reporting suspicious interactions immediately.